RPC-VMware Components
RPC-VMware is composed of a single dedicated VMware vSphere cluster managed by dedicated VMware vCenter Server® or Servers. RPC-VMware includes several core components and optional add-on components.
The core components and some of the optional add-on components require management tools, such as vCenter Server, Platform Services Controller™ (PSC) and VMware NSX Manager™. These must run in the same cluster as the customer’s workloads. The services must always have access to sufficient compute resources or the RPC-VMware functionality and availability are at risk.
To address this requirement, the core and optional add-on management tools run in a designated cluster resource pool, which guarantees access to sufficient resources. The management tools can consume more compute resources in the future as VMware releases newer versions of its software.
Rackspace manages and maintains the RPC-VMware product’s VMware services and infrastructure resources. Any changes to settings or configurations of the VMware-hosted services, networking, storage, and compute systems must be requested by opening a ticket with Rackspace Support.
You can view and manage your virtual systems that you provision from the RPC-VMware services user interfaces (UIs) and APIs.
The following table describes the management services for the core components of RPC-VMware. Your private cloud includes these services.
| Component | Description |
|---|---|
| Management resource pool | A cluster resource pool where the required and optional management services reside. The resource pool is used to restrict access and to manage resources for the management services. The resource pool and the VMs running it are required and are managed by Rackspace. Management services, such as VMware vCenter Server and the PSC, are requirements for providing and managing RPC-VMware. These services must always have access to sufficient compute resources or the RPC-VMware functionality and availability is at risk. To address this requirement, the resource pool is configured to reserve a sufficient amount of CPU and memory resources. The amount of reserved resources could be increased in the future as VMware releases newer versions of their software. |
| Management network | A single VLAN setment behind your firewall exclusively used for the management of RPC-VMware. Rackspace requires network access to management services and infrastructure for monitoring, troubleshooting, and resolution of issues. The customer and Rackspace co-manage the firewall rules. Do not modify the firewall rule set in a manner that prevents Rackspace from accessing the management network and infrastructure as you can negatively impact the Service Level Agreement (SLA). If you do interrupt Rackspace network access by a change to firewall rules, Rackspace reverts or alters the customer created firewall rules and contacts you about the change. This is required due to VMware license reporting requirements for your environment. |
| vCenter Server virtual appliance | Provides centralized visibility, proactive management, and extensibility for VMware vSphere from a single console. vCenter Server is accessible from the vSphere client and the vSphere API. |
| PSC virtual appliances | Provides identity management for users and applications that interact with VMware vSphere and licensing services to RPC-VMware. The PSC is paired directly with the vCenter Server and does not require a separate management interface. |
| NSX® Manager virtual appliance | Provides the graphical user interface (GUI) and the REST APIs for creating, configuring, and monitoring virtual network components. |
| Virtual Machine Recovery (VMR) virtual appliance | Enables image-based backups of the management services which allows Rackspace to quickly recover management services. The VMR appliance is used only by Rackspace and does not back up any of the VMs created by the customer on the compute cluster. No customer access is provided to the VMR appliance. |
| Jump server | Used by Rackspace to gain access to your cluster to maintain the management services. No customer access is provided. |
| vRealize® Operations Manager™ virtual appliance | Provides all vRealize Operations Manager functionality, enabling activities such as checking the health of the hosted VMware environment, performing capacity planning, and proactively eliminating performance bottlenecks. The appliance is accessible via a web interface. |
| vRealize Log Insight virtual appliance cluster | Used by Rackspace to monitor the management services of RPC-VMware. No customer access is provided, however, log message forwarding can be configured on request. Contact your support team for more details. |
| SDDC Manager virtual appliance | Provides orchestration services for the administration of RPC-VMware. This appliance is used only by Rackspace. No customer access is provided. |
| DNS servers | Provide local DNS resolution for the management components of RPC-VMware. No customer access is provided. |
Management services for core components
VMware vSAN for RPC-VMware
VMware vSAN™ is an enterprise-grade, hyperconverged software-defined storage solution optimized for VMware VMs that is natively embedded in the vSphere hypervisor. vSAN provides service-level and policy management at the VM and virtual machine disk (VMDK) level, provides performance quality of service (QoS) capability at the VM level, and allows enterprise-grade scalability for capacity and performance without the need for a large upfront investment.
vSAN enables the use of the Rackspace Private Cloud powered by VMware (RPC-VMware) environment to manage and provision storage through self-service, and to also offer role-based self-service access to other users within the organization. vSAN allows storage policy to be set for availability, performance, and QoS at the VM and VMDK levels, while eliminating the concept of LUN, volume, and RAID to make storage provisioning and management simple for use by a VMware administrator. In addition, vSAN also allows for integration into VMware vRealize® Operations™ and vRealize Automation™ to provide end-to-end Software-Defined Data Center (SDDC) manageability and service delivery.
This handbook is your primary resource for information related to the vSAN component for RPC-VMware, such as getting started, using, and getting help. It also includes references to additional resources external to the handbook.
The vSAN component is not available as a stand-alone product.
- Getting started with vSAN for RPC-VMware
- vSAN and vRealize Operations
- vSAN licensing
- vSAN patching and upgrading
- vSAN API
- Using vSAN for RPC-VMware
- Additional resources for vSAN
Getting started with vSAN for RPC-VMware
This section provides the following information about the vSAN add-on for Rackspace Private Cloud powered by VMware (RPC-VMware):
- vSAN architecture
- vSAN components
- vSAN features
- vSAN roles and permissions
- vSAN managed services
- vSAN spheres of support
- vSAN compatibility
vSAN architecture
The following diagram illustrates the vSAN add-on architecture. The vSAN components are explained in the next section.
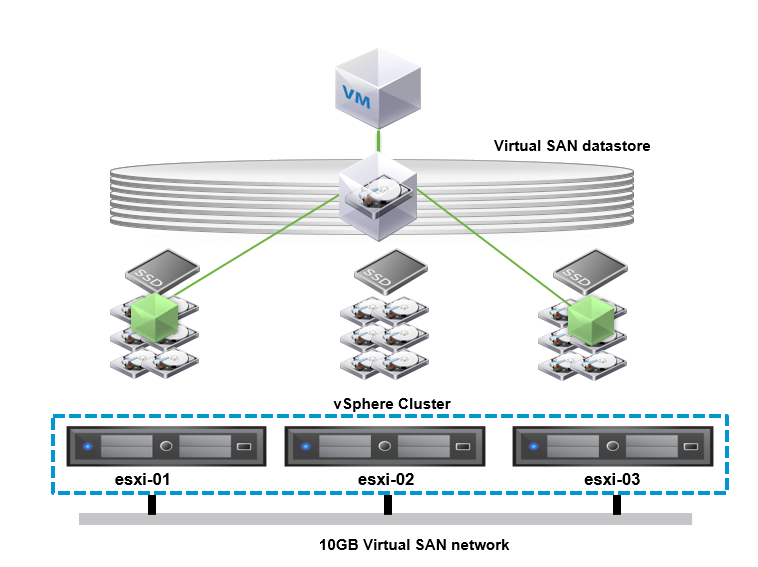
vSAN components
vSAN for Rackspace Private Cloud powered by VMware (RPC-VMware) contains the following components.
| Component | Description |
|---|---|
| Host | ESXi hosts (hypervisors) run the vSAN software and provide the local drives that are used for the cache and capacity tiers. |
| Disk group | A disk group is a unit of physical storage capacity on a host and a group of physical devices that provide performance and capacity to the vSAN cluster. On each ESXi host that contributes its local devices to a vSAN cluster, devices are organized into disk groups. |
| Capacity tier | The capacity tier is used to permanently store data that is stored in vSAN. Cold data not in the cache tier is written to the capacity tier. The capacity tier is made up of flash disks. |
| Cache tier | Each disk group must have one flash cache device and one or more capacity devices. The devices used for caching cannot be shared across disk groups, and cannot be used for other purposes. A single caching device must be dedicated to a single disk group. RPC-VMware uses only all-flash clusters. In an all-flash cluster, flash devices are used for both the cache tier and capacity tier. In all-flash clusters, the cache tier is used to cache writes only. |
| vSAN datastore | The datastore that is provided by vSAN and backed by the aggregate storage of all drives claimed by vSAN. |
| VM storage policy | VM-level availability and performance policies that can be set and modified as needed. vSAN works with VM storage policies to support a VM-centric storage approach. If no storage policy is explicitly assigned to a VM is when it is provisioned, a generic system-defined storage policy called the vSAN Default Storage Policy is automatically applied to the VM. |
| Deduplication and compression | Deduplication and compression occur when data is destaged from the cache tier to the capacity tier. This function is set when you enable “space efficiency” on a cluster level. Deduplication happens on a per disk group basis. Bigger disk groups result in a higher deduplication ratio. After the blocks are deduplicated, they are compressed. |
vSAN features
The following major features are supported in the vSAN add-on for Rackspace Private Cloud Powered by VMware (RPC-VMware):
- All flash
- Distributed RAID
- Flash caching
- High-performance snapshots
- Quality of service (QoS) IOPS limits
- Deduplication and compression
- Storage-based policy management
The following vSAN features are not supported in vSAN for RPC-VMware:
- Rack awareness availability
- Stretched cluster
The vRealize Operations management pack for vSAN is also supported and configured as part of the standard vRealize Operations installation for RPC-VMware.
vSAN roles and permissions
To implement the separation of customer and Rackspace duties in vSAN, Rackspace implements vCenter Server® permissions.
The Customer Access role includes the following privileges to allow customers to run vSAN health checks and to create vSAN storage policies.
vSAN health checks
- Read access to the cluster
- Global.Settings
- Global.Diagnostics
- Virtual Machine.Create
- Virtual Machine.Remove
vSAN storage policies
- Profile-driven storage.Update
- Profile-driven storage.View
vSAN managed services
Rackspace offers 24x7x365 support for Rackspace Private Cloud powered by VMware (RPC-VMware). Rackspace is one of VMware’s largest global Cloud Provider Program partners, with elevated access to technical specialists for rapid resolution of unexpected software-related issues within the VMware stack.
Rackspace VMware Certified Professionals (VCPs) assist in the architecture, deployment, and troubleshooting of the RPC-VMware environment. Rackspace monitors and maintains the VMware software stack, including installing and configuring the RPC-VMware services and any add-on services, backing up and restoring the VMware service VMs as needed, and monitoring the hypervisors for hardware issues and availability.
Rackspace provides the following services for vSAN:
- Installation and initial configuration including optional settings like compression and deduplication
- Monitor for host and disk failure
- Troubleshoot and remediate host and disk failures
- Patch and upgrade
vSAN spheres of support
Rackspace completely manages and supports the vSAN installation and configuration. Rackspace is responsible for keeping the vSAN datastore up and running. Likewise, Rackspace manages and supports the physical hardware, network, and storage infrastructure on which vSAN depends.
Customers are responsible for building VMs in vSAN, managing the disk space usage, and assigning storage policies to VMs.
Rackspace configures and supports the following features:
- Access control
- Alerting/disk replacement
- Distributed RAID
- Flash caching
- Deduplication and compression
- Diskgroup re-configuration
- vSAN networking (VMkernel ports and virtual distributed switch)
The customer configures and uses the following features:
- Capacity management
- High-performance snapshots
- Performance monitoring
- Quality of service (QoS) IOPS limits
- Storage-based policy management
- Storage-policy-based policy management
- vRealize Operations vSAN management
vSAN compatibility
vSAN might not be compatible with all Rackspace products and services. Contact your Rackspace Support specialist for detailed information about whether any specific Rackspace product is compatible with your vSAN.
vSAN compatibility with third-party products
You can access vSAN by using the vSAN API. You can use any third-party management, orchestration, or other type of tools that are compatible with the vSAN API. In this case, the functionality of any such tool is limited by the vSAN features and capabilities as described in this handbook. Ensure that the vSAN API version of your environment is compatible with the third-party tools that you want to use.
vSAN compatibility when elevated permissions are needed
In some cases, existing role permissions provided by Rackspace do not allow a custom or third-party tool to function. Contact the Rackspace account team to determine if role permission adjustments are possible.
vSAN and vRealize Operations
Both vSAN and vRealize Operations are features of Rackspace Private Cloud powered by VMware (RPC-VMware). The vRealize Operations management pack for vSAN is installed by Rackspace. Customers can use the default features of the management packs, such as default reports and dashboards. They can also customize it, such as building custom alerts, reports, and dashboards.
For more information, see the vRealize Operations Management Pack for vSAN 1.0 Guide.
vSAN licensing
For details about licensing, see the main licensing section in the handbook.
vSAN patching and upgrading
For details about patching and upgrading, see the main patching and upgrading section in the handbook.
vSAN maintenance mode types
The following vSAN maintenance modes can be used on a vSAN cluster during patching or upgrading. For each type, some impact and use cases information is provided. Rackspace will coordinate with you to select the vSAN maintenance mode type that best meets your needs.
Ensure accessibility mode
This is the default option. When you power off or remove the host from the cluster, vSAN ensures that all accessible VMs on this host remain accessible. Because the host is now absent from the cluster, the vSAN cluster will wait for one hour, and if the host is not back, rebuild all the components that were located on the host.
Note that this unprotected state lasts until either the hosts exits maintenance mode, or after all components located on the hosts have been rebuilt, which starts one hour after the hosts enters maintenance mode.
Additionally, if a VM goes down because of a component failure while a host is in this maintenance mode, the VM objects will become available again when the hosts exits maintenance mode. The VM will most likely have failed then because it could not access its storage, but it should be possible to restart the VM.
While the host is in maintenance mode, the cluster lets the VMs in the cluster that have components stored on the specific host to invalidate their failure to tolerate (FTT) policy. That is, any VMs in the cluster with a FTT=1 policy that have components on the host will lose one component and are therefore not able to tolerate any failure. The VMs still have enough components to stay up but are not protected from component failure. If anything else fails in the cluster that stores components of the VM, the VM’s storage is lost and the VM will most likely crash.
Select this option if you take the host out of the cluster temporarily (for example, to install upgrades) and plan to have the host back in the cluster. This option is not appropriate when you permanently remove the host from the cluster.
Full data migration mode
vSAN evacuates all data to other hosts in the cluster and maintains or fixes availability compliance for the affected components in the cluster.
This option results in the largest amount of data transfer and consumes the most time and resources.
The host does not enter maintenance mode if a VM object that has data on the host is not accessible and cannot be fully evacuated.
Select this option if you plan to migrate the host permanently.
It can also be used to ensure that VMs with the FTT=1 policy don’t have reduced availability during the maintenance. Note that if the availability requirements of the VMs are that high, it might be better to use FTT=2 policy instead.
When evacuating data from the last host in the cluster, ensure that you migrate the VMs to another datastore and then place the host in maintenance mode.
No data migration mode
vSAN does not evacuate any data from this host.
Any VMs with a FTT value of 1 or higher stay up with reduced availability (similarly to the Ensure Accessibility option), while any VMs with FTT=0 fail.
This option should be used only during a complete cluster migration, when all the hosts need to be shut down, and then only after all VMs have been shut down.
vSAN API
Detailed API documentation is located on the VMware API and SDK Documentation site.
Rackspace does not provide developer support for the APIs for any of the RPC-VMware components. However, Rackspace can coordinate with VMware to address your questions and issues.
Using vSAN for RPC-VMware
This section provides instructions for using the vSAN component of RPC-VMware.
Access control
From vCenter, your customer role uses access control to determine what permissions you have.
Capacity management
For information about managing capacity, see vRealize Operations vSAN Management Pack.
Performance monitoring
For more information, see vRealize Operations vSAN Management Pack.
Quality of service IOPS limits
vSAN includes a quality of service (QoS) feature that limits the number of input/output operations per second (IOPS) that an object can consume.
QoS is a storage-policy-based management (SPBM) rule. Because QoS is applied to vSAN objects through a storage policy, you can apply it to individual components or the entire VM without interrupting the operation of the VM.
QoS for vSAN is normalized to a 32 KB block size, and treats reads the same as writes. An example with an IOPS limit of 500 (regardless of block size up to 32 KB) will result in 500 IOPS, while a block size of 64 KB would result in 250 IOPS. It is important to consider the workload profile when configuring IOPS limits.
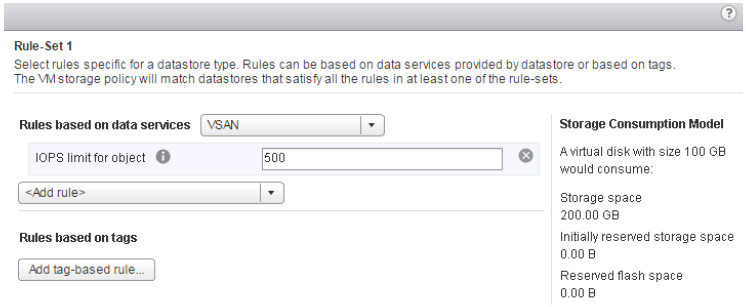
Deduplication and compression
The deduplication and compression feature is enabled on VSAN clusters based on customer responses to implementation questions. It requires the correct number of hosts and all flash storage. The amount of storage reduction from deduplication and compression cannot be configured or guaranteed. It depends on many factors, including the type of data stored and the number of duplicate blocks. For example, the deduplication ratio tends to increase in new clusters as data is added and the opportunity to find duplicate data blocks rises.
If a customer does not elect to enable deduplication and compression initially, but chooses to enable it at a later date, the customer must submit a ticket requesting the change and specify whether or not they will allow reduced redundancy while the change is being applied. Enabling deduplication and compression requires a rolling reformat of every disk group on every host. To accomplish this change, Virtual SAN evacuates data from the disk group, removes the disk group, and recreates it with a new format that supports deduplication and compression. The enablement operation does not require virtual machine migration or DRS. In certain environments, your Virtual SAN cluster might not have enough resources for the disk group to be fully evacuated. You may still be able to enable deduplication and compression using the Allow Reduced Redundancy option. This option keeps the VMs running, but the VMs might be unable to tolerate the full number of failures defined in the VM storage policy. As a result, temporarily during the format change for deduplication and compression, your virtual machines might be at risk of experiencing data loss. Virtual SAN restores full compliance and redundancy after the format conversion is completed.
Storage-based policy management
Users with the appropriate role and permission can create and administer VMs and policies.
Each VM deployed on vSAN contains a set of objects, such as VMDKs and snapshots. Each object contains a set of components determined by the capabilities configured in the VM storage policy. If the policy contains a stripe width, the associated object is striped across multiple devices in the capacity tier. Each stripe is a component of the object.
vSAN might stripe an object across multiple disks, even if the policy is one stripe. Normally, this action occurs when an administrator requests the creation of a VMDK that is too large to fit on a single physical drive. Because the maximum component size is 255 GB, objects that are greater than 255 GB are automatically be divided into multiple components. For example, if an administrator deploys a 2 TB VMDK, eight or more components are created in the same RAID-0 stripe configuration.
For a walkthrough of assigning policies, see the VMware product walk-throughs site.
vRealize Operations vSAN Management Pack
The vRealize Operations Management Pack for vSAN is installed and configured by default in RPC-VMware. To use the management pack, see the Connecting to vRealize Operations section in the vRealize Operations handbook for instructions about logging in.
With the vSAN management pack, you can perform the following tasks:
- Monitor and proactively alert on vSAN problems via Alert Groups for health, capacity, and configuration (based on the vSAN health checks).
- Identify vSAN clusters running out of capacity now or soon.
- Compare non-vSAN and vSAN clusters to deploy or balance workloads and optimize for performance and utilization.
For a walkthrough of using the management pack, see the VMware Feature Walkthrough site.
Health checks
Customers can view health checks. For a walkthrough of this feature, see the VMware Feature Walkthough site.
VMware recommends that you use the Health Check plug-in to perform initial triage of any vSAN problems. A detailed description of the operational aspects of the health check are located in the VMware Virtual SAN Health Check Plugin Guide.
Additional resources for vSAN
See the following resources for more information about vSAN:
- VMware product information
- VMware hands-on labs
- Official VMware documentation
- VMware YouTube channels
- VMware storage and availability technical documents
- VMware product walk-throughs
VMware NSX for RPC-VMware
VMware NSX® is the network virtualization platform for the Software-Defined Data Center (SDDC), delivering the operational model of a VM for entire networks. With NSX, network functions including switching, routing, and firewalling are embedded in the hypervisor and distributed across the environment. This effectively creates a “network hypervisor” that acts as a platform for virtual networks and services.
Like the operational model of VMs, virtual networks are programmatically provisioned and managed independently of underlying hardware. NSX reproduces the entire network model in software, enabling any network topology— from simple to complex multitier networks— to be created and provisioned in seconds. Users can create multiple virtual networks with diverse requirements, leveraging a combination of the services offered via NSX to build inherently more secure environments.
This handbook is your primary resource for information related to NSX for RPC-VMware. Such as, getting started, using, and getting help. It also includes references to additional resources external to the handbook.
NSX is not available as a stand-alone product.
- Getting started with NSX for RPC-VMware
- Optional add-on for NSX
- NSX licensing
- NSX patching and upgrading
- NSX API
- Using NSX for RPC-VMware
- Additional resources for NSX
Getting started with NSX for RPC-VMware
This section provides the following information about the NSX component of Rackspace Private Cloud powered by VMware (RPC-VMware):
- NSX architecture
- NSX components
- NSX features
- NSX roles and permissions
- NSX managed services
- NSX spheres of support
- NSX compatibility
- NSX authentication methods
- NSX Use Cases
- Multi-tier Network Use Case
- Dynamic Routing Use Case
NSX architecture
The following diagram shows how NSX fits into the architecture of Rackspace Private Cloud powered by VMware (RPC-VMware). The NSX Manager™ resides in the management resource pool. During the initial configuration of NSX, three NSX Controllers™ are deployed in the cluster. Continuing with the configuration process, VXLAN Tunnel Endpoints (VTEPs) are deployed on the hypervisor so the hypervisor itself can act as an endpoint to NSX. The VTEPs are deployed to a dedicated VLAN, and this VLAN is the base for the VXLAN overlay networks that are created and managed by NSX.
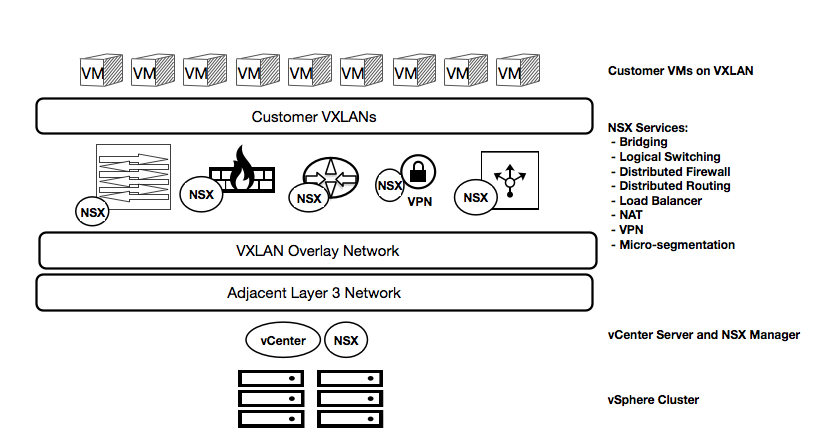
NSX components
The following table describes each component of NSX for RPC-VMware.
| Component | Count | Description |
|---|---|---|
| NSX Manager | 1 | Provides an aggregated system view and is the centralized network management component of NSX. NSX Manager is installed as a virtual appliance on any ESXi host in your vCenter environment. |
| NSX Controller | 3 | The central control point for all logical switches within a network. Controllers maintain information about all VMs, hosts, logical switches, and VXLANs. |
| VTEP | NA | Every ESXi host enabled for NSX is configured with an additional VMkernel port used as a VXLAN Tunnel End Point (VTEP). In other words, a VTEP is a host interface that forwards Ethernet frames from a virtual network via VXLAN or vice-versa. |
| VXLAN | NA | Virtual Extensible LAN (VXLAN) is a encapsulation protocol for running an overlay network on existing layer 3 infrastructure. An overlay network is a virtual network that is built on top of existing network layer 2 and layer 3 technologies to support software defined networks. |
NSX features
This section lists the features of the NSX that are available for your use within the RPC-VMware environment and your customer permissions. Features not listed here either need to be performed by Rackspace (see the NSX managed services section) or might be unavailable within the RPC-VMware product and its add-on services.
| Feature | Description |
|---|---|
| Switching | Enable logical layer 2 overlay extensions across a routed (L3) fabric within and across data center boundaries. Support for VXLAN-based network overlays. |
| Routing | Provides routing between virtual networks performed in a distributed manner in the hypervisor kernel. |
| Distributed firewalling | Provides distributed stateful firewalling embedded in the hypervisor kernel. Additionally, NSX can also provide north-south firewall capability through NSX Edge™. |
| Load balancing | Provides an L4–L7 load balancer with SSL offload and pass-through, server health checks, and App Rules for programmability and traffic manipulation. |
| VPN | Provides site-to-site and remote-access VPN capabilities, and unmanaged VPN for cloud gateway services. |
| NSX gateway | Provides support for VXLAN-to-VLAN bridging for seamless connection to physical workloads. |
| NSX API | Provides a RESTful API for integration into any cloud management platform or custom automation. |
| Dynamic security policy | NSX service composer enables the creation of dynamic security groups. Beyond IP address and MAC, membership of security groups can be based on vCenter objects and tags, operating system type, and Active Directory roles to enable a dynamic security enforcement capability. |
| Third-party partner integration | Provides support for management, control plane, and data plane integration with third-party partners in a wide variety of categories. Third-party integration configuration might require assistance from your Rackspace Support team. If you are interested in enabling third-party integration, contact your Support team for more details. |
NSX roles and permissions
Customers are given the Enterprise Administrator role to NSX in the RPC-VMware product. However, an Enterprise Administrator can allocate lesser roles to individuals to match their job responsibilities.
| Role | Permissions |
|---|---|
| Auditor | Users in this role can only view system settings and auditing, events and reporting information, but cannot make any configuration changes. |
| Security Administrator | Users in this role can configure security compliance policies, and can view the reporting and auditing information in the system. |
| NSX Administrator | Users in this role can perform all tasks related to deployment and administration of the NSX Manager instance. |
| Enterprise Administrator | Users in this role can perform all tasks related to deployment and configuration of NSX products and administration of the NSX Manager instance. |
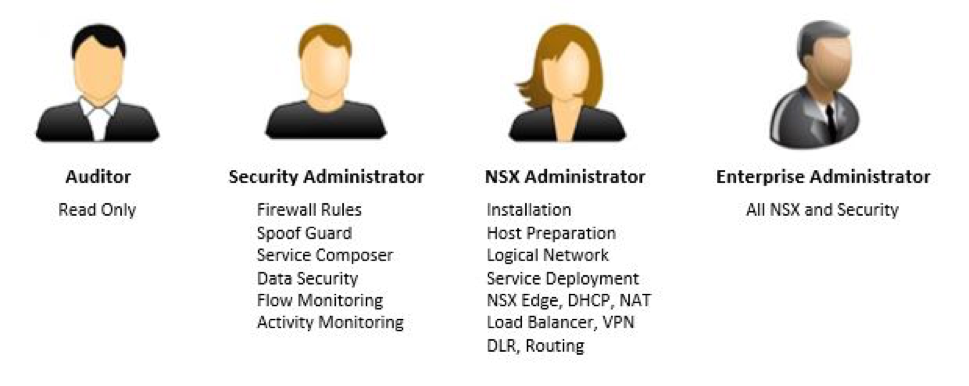
NSX managed services
Rackspace offers 24x7x365 support for Rackspace Private Cloud powered by VMware (RPC-VMware). Rackspace is one of VMware’s largest global Cloud Provider Program partners, with elevated access to technical specialists for rapid resolution of unexpected software-related issues within the VMware stack.
Rackspace’s VMware Certified Professionals (VCPs) assist in the architecture, deployment, and troubleshooting of the RPC-VMware environment. Rackspace monitors and maintains the VMware software stack, including installing and configuring the RPC-VMware services and any add-on services, backing up and restoring the VMware service VMs as needed, and monitoring the hypervisors for hardware issues and availability.
Rackspace provides the following services for NSX:
- Installation and initial configuration
- Monitor for NSX Manager failure
- Troubleshoot and remediate NSX Manager failures
- Patch and upgrade of NSX components
NSX spheres of support
The NSX appliance and all supporting infrastructure are supported by Rackspace. Internally, we use Rackspace Monitoring to monitor the health of the NSX appliance. The support of the underlying networking of the NSX environment is also supported by Rackspace.
The following table outlines customer and Rackspace responsibilities related to NSX.
| Rackspace | Customer | |
|---|---|---|
| Registering NSX Manager with vCenter | x | |
| Licensing of NSX | x | |
| Initial customer permissions entitlements | x | |
| Create IP pools for initial configuration | x | |
| Deploy VTEPs (host preparation) | x | |
| Deploy NSX controllers | x | |
| Troubleshooting infrastructure | x | |
| Configure transport zones | x | |
| Configure VXLAN (host preparation) | x | |
| Create an NSX Edge | x | |
| Deploy a distributed logical router | x | |
| Deploying VXLANs | x | |
| Give access to customer-created role | x |
NSX compatibility
NSX for RPC-VMware might not be compatible with all Rackspace products and services. Contact your Rackspace Support specialist for detailed information about whether any specific Rackspace product is compatible with NSX for RPC-VMware.
The NSX version used with your RPC-VMware environment is compatible with all other components in RPC-VMware. Upgrades are only performed only if the upgrade is compatible with all the other components in RPC-VMware.
NSX compatibility with third-party products
NSX can be accessed by using the NSX API. You can use any third-party management, orchestration, or other type of tools that are compatible with the NSX API. In this case, the functionality of any such tool will be limited by the NSX features and capabilities as described in this handbook. Ensure that the NSX API version of your environment is compatible with the third-party tools that you want to use.
NSX compatibility when elevated permissions are needed
In some cases, existing role permissions provided by Rackspace do not allow a custom or third-party tool to function. Contact the Rackspace account team to determine if role permission adjustments are possible.
NSX authentication methods
The customer can use the same authentication methods that are used with vCenter to access the NSX section of the web client. However, you may have to work with Rackspace support to import groups or individuals into vCenter from your on-premises AD. Once these groups or individuals are added to vCenter you need to give them the permission level desired through the NSX section in the web client.
NSX Use Cases
The following references are some sample customer use cases for NSX for Rackspace Private Cloud Powered by VMware (RPC-VMware):
Multi-tier Network Use Case
NSX provides you the ability to create multiple networks in your private cloud for various purposes, such as providing logical network segments for a 3 tier application. In this use case, 3 logical switches, a distributed router and distributed firewall provide logical web-tier, app-tier and db-tier network segments, including the appropriate routing and security between the tiers.
The distributed logical router (DLR) provides network routing between the web-tier and the app-tier. It also provides routing between the app-tier and db-tier. No routing is provided between the web-tier and db-tier.
The distributed firewall (DFW) only allows restricted necessary network communication between the web-tier and the application tier. The DFW rules can be granularly limited based on parameters such as the source and target VMs and types of traffic (such as by TCP port number).
Additionally, the DLR an be configured to allow routing to an external network via an NSX Edge Gateway. In this case, the DFW and the NSX Edge firewalls can be used to permit, granularly controlled communication between the external network and the web-tier, while completely disallowing any external communication with the other tiers.
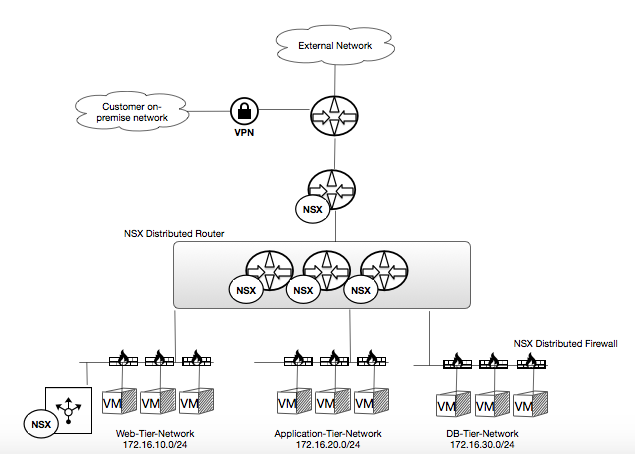
Additionally, a “one-armed” edge device can be used to provide additional network services in the web-tier, such as load balancing and DHCP.
REF: https://blogs.vmware.com/networkvirtualization/2014/07/getting-started-vmware- nsx-part-ii-building-virtual-networks.html/
Dynamic Routing Use Case
The physical firewall used to protect your RPC-VMware private cloud is not configured with dynamic routing. So, in order to allow your on-premise network or other external networks to communicate to your NSX network segments, you will need to request that Rackspace configure statics routes on the physical firewall. Consider requesting a summary route for all networks you may build in the NSX environment
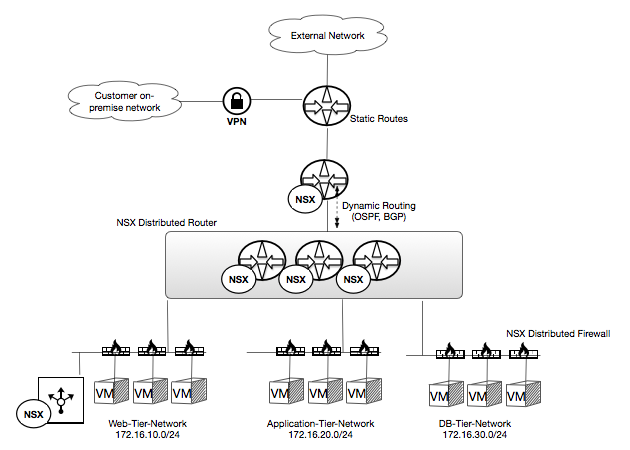
Alternatively, you can choose to terminate your VPN to the NSX Edge, instead of the physical firewall. To facilitate this, the DLR and the NSX Edge can be configured to use dynamic routing, ensuring the NSX Edge is aware of the available, routed networks provided by the DLR.
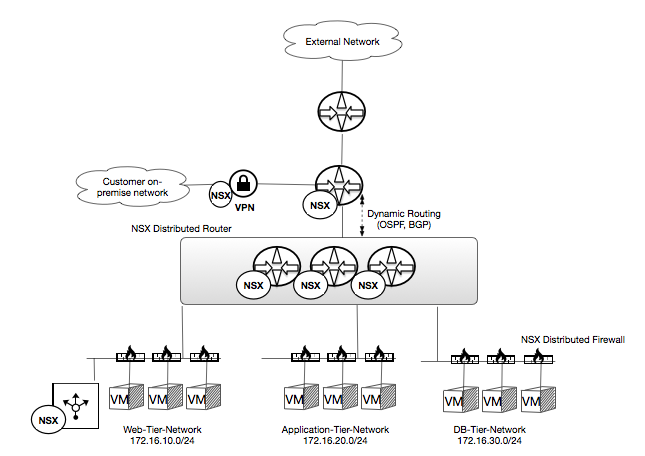
Optional add-on for NSX
Customers can add service deployments to their NSX environment. A service deployment is a partner service offered by a third-party company. This partner service could be a third-party firewall or a guest introspection service, for example. Rackspace does not provide managed services for any partner service not installed by Rackspace and makes no guarantees that all partner services will work with NSX for RPC-VMware.
NSX licensing
For details about licensing, see the main licensing section in the handbook.
NSX patching and upgrading
For details about patching and upgrading, see the main patching and upgrading section in the handbook.
NSX API
Detailed API documentation is located on the VMware API and SDK Documentation site.
Rackspace does not provide developer support for the vCenter API, vSAN API, or the APIs for any of the RPC-VMware add-ons. However, Rackspace can coordinate with VMware to address your questions and issues.
Using NSX for RPC-VMware
If you want to add individuals or groups to NSX roles, the NSX Enterprise Administrator must add them to the NSX roles through the NSX permissions section in the vSphere web client.
Rackspace configures NSX and the underlying infrastructure so that you can begin to tailor the NSX environment to your needs. Rackspace follows VMware best practices by deploying three NSX controllers for the environment. VMware only supports the use of only three controllers, even though it is possible to add and subtract controllers. If you remove or add NSX controllers, you will be outside of VMware’s and Rackspace’s support requirements.
Caution: It is possible for you to create Distributed Firewall rules that could block all traffic in and out of the VMs. Take extra care when creating these types of rules in NSX.
Additional resources for NSX
The following resources are recommended for more information:
- VMware product information
- VMware Hands-On Labs
- Official VMware documentation
- VMware YouTube channels
- VMware Storage and Availability Technical Documents
- VMware Product Walkthroughs
VMware vRealize Operations for RPC-VMware
VMware® vRealize® Operations™ helps you manage performance utilization and capacity visualization of the Rackspace-hosted virtualized infrastructure. vRealize Operations Endpoint Operations Management provides additional visibility into the guest-OS layer and helps you monitor in-guest services and the following applications: Microsoft® SQL Server™, Microsoft Active Directory®, Apache® Tomcat™, and PostgreSQL®.
vRealize Operations collects and analyzes information from multiple data sources and uses advanced analytics algorithms to learn and recognize the “normal” behavior of every object that it monitors. Through dashboard views and reports, you can view details so you can make informed decisions in the following areas:
- Issue resolution and root cause analysis
- Environment health and advanced warning of potential issues
- Capacity management and forecasting
vRealize Operations uses management packs to collect, analyze, and present data from many VMware and third-party data sources, which provides a holistic view of the RPC-VMware infrastructure and workloads.
This handbook is your primary resource for information related to the vRealize Operations component of Rackspace Private Cloud powered by VMware (RPC-VMware), such as getting started, using, and getting help. It also includes references to additional resources external to the handbook.
The vRealize Operations component is not available as a stand-alone product.
- Getting started with vRealize Operations for RPC-VMware
- vRealize Operations licensing
- vRealize Operations patching and upgrading
- vRealize Operations API
- Additional resources for vRealize Operations
Getting started with vRealize Operations for RPC-VMware
This section provides the following information about the VMware vRealize Operations component of Rackspace Private Cloud powered by VMware (RPC-VMware):
- vRealize Operations architecture
- vRealize Operations components
- vRealize Operations features
- vRealize Operations roles and permissions
- vRealize Operations managed services
- vRealize Operations spheres of support
- vRealize Operations compatibility
- vRealize Operations authentication methods
- Connecting to vRealize Operations
vRealize Operations licensing
For details about licensing, see the main licensing section in the handbook.
vRealize Operations patching and upgrading
For details about patching and upgrading, see the main patching and upgrading section in the handbook.
vRealize Operations API
VMware provides full documentation on how the API workflows are performed and lists of the API commands in the vRealize Operations Manager API Programming Guide.
Additional resources for vRealize Operations
The following resources are recommended for vRealize Operations:
Updated over 1 year ago
