Application Credentials in the Rackspace Cloud
What are Application Credentials in the Rackspace Cloud and how to manage them.
What Are Application Credentials?
Application Credentials are a feature in Rackspace Cloud, by way of Identity (Keystone), that allow users to create limited-access tokens for applications or scripts without exposing their primary user password.
They provide a secure and manageable way to let applications authenticate with OpenStack services using a pair of:
- Application Credential ID (or Name)
- Secret (like a password)
Think of them as service accounts or API keys for specific apps, with restricted access and scopes.
IMPORTANT: You cannot use an Application Credential to log into Skyline. Application Credentials are not like normal users and are instead designed for non-interactive, programmatic access — such as scripts, API clients, or automation tools.
Use Cases
- Allowing automation tools to access your Rackspace Cloud account without storing your user’s main password
- Delegating limited access to an external tool or team
- Running background tasks or scheduled jobs
- CI/CD pipelines needing programmatic access to OpenStack APIs
How They Differ from Normal Users
| Feature | Normal User Credentials | Application Credentials |
|---|---|---|
| Tied to a User | Yes | Yes (but scoped access¹) |
| Uses Main Password | Yes | No (uses a separate secret) |
| Supports Scoped Access¹ | Indirectly via roles | Yes (can restrict role, project, service) |
| Can Be Rotated | Not as easily | Yes (create/revoke without affecting the user) |
| Risk If Leaked | Full account compromised | Limited to scope¹ of the application credential |
| Skyline Access | Yes | No |
¹ scoped access means that a user's permissions are limited to a specific subset of resources, locations, or functions rather than being system-wide
Managing Application Credentials in Skyline UI
Skyline is Rackspace Cloud's modern web-based dashboard. If you're unfamiliar with accessing or managing your account via the Skyline UI, see this document first
Steps to Create Application Credentials
-
Log in to the Skyline Dashboard with your user credentials.
-
Click the User Icon in the top right and select User Center
-
Click Application Credentials from the left-hand navigation bar.
-
Click Create Application Credentials
-
Fill out the creation form:
- Name: A friendly identifier (e.g.,
my-deploy-tool) - Expires At (optional): A date which the Application Credential will become invalidated.
- Roles: Choose the minimal roles this app needs (e.g.,
reader) - Unrestricted (optional): Whether this Application User can create or destroy application credentials.
- Description (optional): Details on what this Application Credential is for.
- Name: A friendly identifier (e.g.,
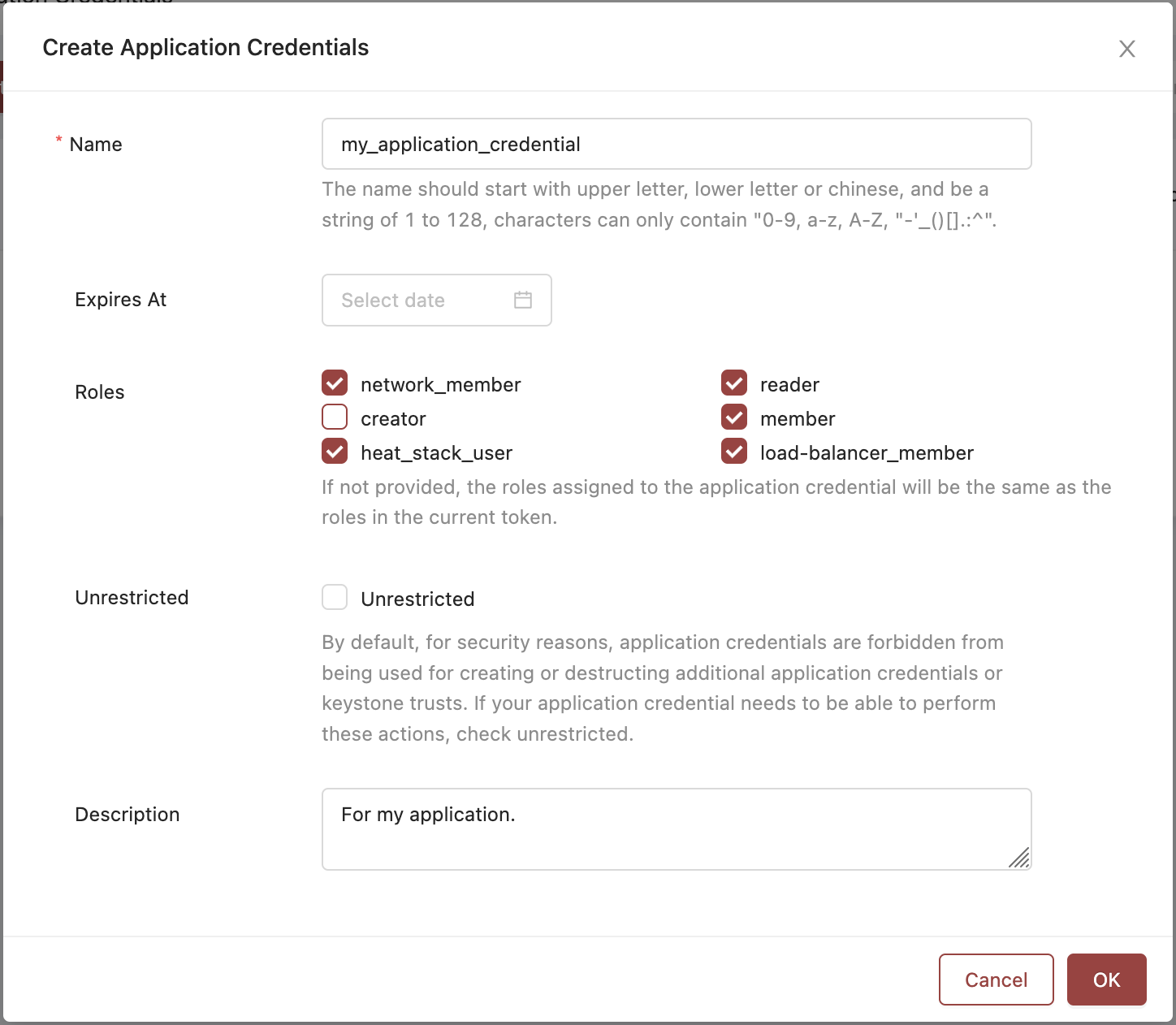
An example of an Application Credential without an expiration. This user also is restricted and cannot manage other Application Credentials, nor can they create resources due to lacking the 'creator' role.
- Click OK
- Open the JSON File that is automatically downloaded. After creation, your browser should automatically download a JSON file with the name of the Application Credential. Within this file is the secret which is essentially the password for that Application Credential. You'll also see some other details for the credential. Below is an example of the contents of one of these files.
{
"id": "12d304f3f5ca678c9dd20e59f04188a1",
"description": "Test_User",
"project_id": "123b456702c738d12345678910e9d95a",
"expires_at": "2025-07-04T04:59:59.999000",
"secret": "7IVY2fIIbsUpRozxmz8xh9briWGyq-Xq9-J6UoqKIz5oIslAvf85TZ29u2K5-slAvf85TZ29-lhLYC4_NxKKw"
}Viewing Existing Application Credentials
-
Log in to the Skyline Dashboard with your user credentials.
-
Click the User Icon in the top right and select User Center
-
Click Application Credentials from the left-hand navigation bar.
-
You can see:
• Name
• Project
• Expiration
• Restriction Status
• Description
• Roles
IMPORTANT: Credentials cannot be edited, only revoked and/or recreated!
Revoking Application Credentials
- In the Application Credentials list, click Delete next to the desired credential
- Select Confirm
- The Application Credential will now be revoked and no longer listed. Once revoked, that credential ID/secret pair will no longer work.
Example: Using Application Credentials with OpenStack CLI
export OS_AUTH_TYPE=v3applicationcredential
export OS_AUTH_URL=https://keystone.api.dfw3.rackspacecloud.com/v3
export OS_APPLICATION_CREDENTIAL_ID=<app_cred_id>
export OS_APPLICATION_CREDENTIAL_SECRET=<app_cred_secret>Now you can use openstack CLI commands without relying on your username/password or an unscoped token.
Troubleshooting Application Credential Failures with the CLI
When trying to use Application Credentials with an older version of the OpenStack CLI, you may see an error like:
Invalid input for field 'identity/password/user/password': None is not of type 'string'This happens because the CLI is falling back to password-based authentication, even though you’re trying to use an Application Credential. The underlying cause is that older distributions (such as Ubuntu/Debian packages) ship with an outdated version of the following:
- python-openstackclient
- keystoneauth1
These versions didn’t yet support the Application Credential authentication plugin. In order to ensure you're using a version that supports the proper authentication method for Application Credentials, be sure you're using the following:
| Component | Required Version | Purpose |
|---|---|---|
python-openstackclient | 5.5.0+ | CLI support for --os-application-credential-id |
keystoneauth1 | 5.1.0+ | Authentication backend for Application Credentials |
openstacksdk | 1.3.0+ | (For Python scripts) Supports auth_type='v3applicationcredential' |
If your installed version is older than these, the CLI will try to use the legacy password flow, fail to find a password field, and return the error mentioned previously.
Check Your Current CLI Version
To check which version of the CLI components you're using - run the following command:
openstack --versionYou can also check the underlying authentication library:
python3 -m pip show keystoneauth1 | grep VersionSecurity Considerations
- Keep secrets in a secure secret store or environment variable
- Follow the rule of least privilege
- Revoke unused or compromised credentials immediately
- Rotate credentials regularly
- Avoid hardcoding secrets in code
Updated about 2 months ago