SDDC Busines Roles and Permissions
SDDC Busines Roles and Permissions
vCenter Roles and Permissions
To implement the separation of customer and Rackspace duties in SDDC Business, Rackspace uses built-in and custom roles in the vCenter Server. Rackspace assigns you a maximum permission role (customer role) and any lesser privileged roles that you request for specific users or groups.
Customers have permissions to create, delete, and manage VMs within their private cloud. Rackspace manages and maintains the ESXi hosts, the vCenter Server, Jump and SVS servers, and additional management VMs as required by the SDDC Business solution. Customers therefore have limited permissions on hosts and management servers.
Specific resource pools and folders are created to house customer created VMs and ensure separation from management VMs. In support of this separation, customers are granted permissions to create, delete, and manage VMs in the Compute-ResourcePool resource pool and in the Workloads and Templates virtual machine folders.
If required for organisational or resource management purposes, customers can create new resource pools below the Compute-ResourcePool and new folders below the Workloads and Templates VMs folders.
The following permission sets are predefined in the vCenter Server:
- Customer Access
- VM Power User
- VM User
- Read Only
Customer Access permission set is a product of permissions applied to two sets of roles. A lower permission set is enforced at the root of the inventory tree, and a higher permission set is applied at the resource pool level of the inventory tree.
The following table shows which vCenter Server permissions are available to each role.
| Permission | Customer Access | VM Power User | VM User | Read Only |
|---|---|---|---|---|
| Alarms | Full Access | No Access | No Access | No Access |
| Datastores | Limited Access | Limited Access | No Access | No Access |
| Network | Limited Access | No Access | No Access | No Access |
| Performance | Full Access | No Access | No Access | No Access |
| Resource | Full Access | No Access | No Access | No Access |
| ScheduledTask | Full Access | Full Access | Full Access | No Access |
| Tasks | Full Access | Full Access | Full Access | No Access |
| vApp | Full Access | Full Access | No Access | No Access |
| Virtual Machine | Full Access | Full Access | Limited Access | No Access |
| Datacenter | Limited Access | Full Access | Limited Access | No Access |
| Global | Limited Access | Limited Access | Limited Access | No Access |
| Host | Limited Access | No Access | No Access | No Access |
| Sessions | Limited Access | No Access | No Access | No Access |
| Storage Views | Limited Access | No Access | No Access | No Access |
| Datastore cluster | Full Access | No Access | No Access | No Access |
| Distributed virtual switch | No Access | No Access | No Access | No Access |
| Distributed virtual port group | No Access | No Access | No Access | No Access |
| ESX agent manager | No Access | No Access | No Access | No Access |
| Extension | No Access | No Access | No Access | No Access |
| vCenter inventory service | No Access | No Access | No Access | No Access |
| vSphere update manager | No Access | No Access | No Access | No Access |
| VRM policy | No Access | No Access | No Access | No Access |
| vService | No Access | No Access | No Access | No Access |
| vSphere Tagging | Full Access | No Access | No Access | No Access |
Authentication Methods
SDDC Business customers have two choices for vCenter authentication:
- Rackspace-provided Active Directory service
- Customer-provided Active Directory service
By default Rackspace is added to every SDDC Business environment at build time. This is to allow our support staff to assist our customer and for day two operations
To check the current authentication sources, click on the vSphere Client menu then click on Administration.
Click on configuration.

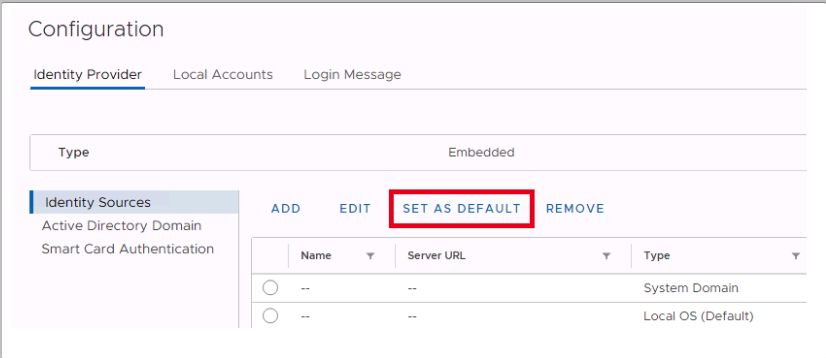
To add your Active Directory as an Identity source please raise a request with our support, the below information is required.
| Configuration Item | Description |
|---|---|
| Name | Label for identification |
| Base DN for users | The Distinguished Name (DN) of the starting point for directory server searches. |
| Base distinguished name for Groups | The Distinguished Name (DN) of the starting point for directory server searches. |
| Domain Name | Your domain name. Example: “domain.local” |
| Domain Alias | Your NetBIOS name. Example: “Domain” |
| Username | Domain user with at least browse privileges. Example: “[email protected]” |
| Primary Server URL | ldap://ipaddress:3268 |
| Secondary Server URL (Optional) | ldap://ipaddress:3268 |
Secondary Server URL (Optional) | ldap://ipaddress:3268 |
Updated 3 months ago